|
Open-Transactions
0.93.0-ge03d287
|
|
Open-Transactions
0.93.0-ge03d287
|
#include <OTSmartContract.hpp>
Public Member Functions | |
| virtual void | SetDisplayLabel (const std::string *pstrLabel=nullptr) |
| const OTString & | GetLastSenderUserID () const |
| const OTString & | GetLastSenderAcctID () const |
| const OTString & | GetLastRecipientUserID () const |
| const OTString & | GetLastRecipientAcctID () const |
| int32_t | GetCountStashes () const |
| int32_t | GetCountStashAccts () const |
| virtual bool | Compare (OTScriptable &rhs) const |
| virtual bool | CanRemoveItemFromCron (OTPseudonym &theNym) |
| virtual void | HarvestOpeningNumber (OTPseudonym &theNym) |
| virtual void | HarvestClosingNumbers (OTPseudonym &theNym) |
| void | CloseoutOpeningNumbers (OTPseudonym *pSignerNym=nullptr) |
| void | HarvestClosingNumbers (OTPseudonym *pSignerNym=nullptr, std::set< OTParty * > *pFailedParties=nullptr) |
| virtual bool | ProcessCron () |
| virtual bool | HasTransactionNum (const int64_t &lInput) const |
| virtual void | GetAllTransactionNumbers (OTNumList &numlistOutput) const |
| virtual bool | AddParty (OTParty &theParty) |
| virtual bool | ConfirmParty (OTParty &theParty) |
| EXPORT bool | SetServerIDIfEmpty (const OTIdentifier &theID) |
| EXPORT bool | VerifySmartContract (OTPseudonym &theNym, OTAccount &theAcct, OTPseudonym &theServerNym, bool bBurnTransNo=false) |
| EXPORT void | PrepareToActivate (const int64_t &lOpeningTransNo, const int64_t &lClosingTransNo, const OTIdentifier &theUserID, const OTIdentifier &theAcctID) |
| bool | CanCancelContract (std::string str_party_name) |
| void | SetRemainingTimer (std::string str_seconds_from_now) |
| std::string | GetRemainingTimer () const |
| bool | MoveAcctFundsStr (std::string from_acct_name, std::string to_acct_name, std::string str_Amount) |
| bool | StashAcctFunds (std::string from_acct_name, std::string to_stash_name, std::string str_Amount) |
| bool | UnstashAcctFunds (std::string to_acct_name, std::string from_stash_name, std::string str_Amount) |
| std::string | GetAcctBalance (std::string from_acct_name) |
| std::string | GetStashBalance (std::string stash_name, std::string asset_type_id) |
| std::string | GetAssetTypeIDofAcct (std::string from_acct_name) |
| bool | SendNoticeToParty (std::string party_name) |
| bool | SendANoticeToAllParties () |
| void | DeactivateSmartContract () |
| virtual void | RegisterOTNativeCallsWithScript (OTScript &theScript) |
| OTStash * | GetStash (std::string str_stash_name) |
| EXPORT void | ExecuteClauses (mapOfClauses &theClauses, OTString *pParam=nullptr) |
| EXPORT bool | StashFunds (const mapOfNyms &map_NymsAlreadyLoaded, const int64_t &lAmount, const OTIdentifier &PARTY_ACCT_ID, const OTIdentifier &PARTY_USER_ID, OTStash &theStash) |
| EXPORT | OTSmartContract () |
| EXPORT | OTSmartContract (const OTIdentifier &SERVER_ID) |
| virtual EXPORT | ~OTSmartContract () |
| void | InitSmartContract () |
| virtual void | Release () |
| void | Release_SmartContract () |
| void | ReleaseStashes () |
| virtual bool | IsValidOpeningNumber (const int64_t &lOpeningNum) const |
| virtual int64_t | GetOpeningNumber (const OTIdentifier &theNymID) const |
| virtual int64_t | GetClosingNumber (const OTIdentifier &theAcctID) const |
| virtual int32_t | ProcessXMLNode (irr::io::IrrXMLReader *&xml) |
| virtual void | UpdateContents () |
| virtual bool | SaveContractWallet (std::ofstream &ofs) const |
 Public Member Functions inherited from opentxs::OTCronItem Public Member Functions inherited from opentxs::OTCronItem | |
| OTCronItem () | |
| bool | DropFinalReceiptToInbox (const OTIdentifier &USER_ID, const OTIdentifier &ACCOUNT_ID, const int64_t &lNewTransactionNumber, const int64_t &lClosingNumber, const OTString &strOrigCronItem, OTString *pstrNote=nullptr, OTString *pstrAttachment=nullptr, OTAccount *pActualAcct=nullptr) |
| bool | DropFinalReceiptToNymbox (const OTIdentifier &USER_ID, const int64_t &lNewTransactionNumber, const OTString &strOrigCronItem, OTString *pstrNote=nullptr, OTString *pstrAttachment=nullptr, OTPseudonym *pActualNym=nullptr) |
| void | HookActivationOnCron (OTPseudonym *pActivator, bool bForTheFirstTime=false) |
| void | HookRemovalFromCron (OTPseudonym *pRemover, int64_t newTransactionNo) |
| bool | IsFlaggedForRemoval () const |
| void | FlagForRemoval () |
| void | SetCronPointer (OTCron &theCron) |
| void | SetCreationDate (const time64_t &CREATION_DATE) |
| const time64_t & | GetCreationDate () const |
| EXPORT bool | SetDateRange (time64_t VALID_FROM=OT_TIME_ZERO, time64_t VALID_TO=OT_TIME_ZERO) |
| void | SetLastProcessDate (const time64_t &THE_DATE) |
| const time64_t & | GetLastProcessDate () const |
| void | SetProcessInterval (const int64_t &THE_DATE) |
| const int64_t & | GetProcessInterval () const |
| OTCron * | GetCron () const |
| void | setServerNym (OTPseudonym *serverNym) |
| void | setServerId (OTIdentifier *serverId) |
| EXPORT bool | SaveCronReceipt () |
| EXPORT bool | SaveActiveCronReceipt (const OTIdentifier &theNymID) |
| virtual | ~OTCronItem () |
| void | InitCronItem () |
| void | Release_CronItem () |
| EXPORT bool | GetCancelerID (OTIdentifier &theOutput) const |
| EXPORT bool | IsCanceled () const |
| EXPORT bool | CancelBeforeActivation (OTPseudonym &theCancelerNym) |
| EXPORT int64_t | GetClosingTransactionNoAt (uint32_t nIndex) const |
| EXPORT int32_t | GetCountClosingNumbers () const |
| EXPORT void | AddClosingTransactionNo (const int64_t &lClosingTransactionNo) |
| EXPORT int64_t | GetOpeningNum () const |
| EXPORT int64_t | GetClosingNum () const |
 Public Member Functions inherited from opentxs::OTTrackable Public Member Functions inherited from opentxs::OTTrackable | |
| OTTrackable () | |
| OTTrackable (const OTIdentifier &SERVER_ID, const OTIdentifier &ASSET_ID) | |
| OTTrackable (const OTIdentifier &SERVER_ID, const OTIdentifier &ASSET_ID, const OTIdentifier &ACCT_ID, const OTIdentifier &USER_ID) | |
| virtual | ~OTTrackable () |
| void | InitTrackable () |
| void | Release_Trackable () |
| int64_t | GetTransactionNum () const |
| void | SetTransactionNum (int64_t lTransactionNum) |
| const OTIdentifier & | GetSenderAcctID () const |
| const OTIdentifier & | GetSenderUserID () const |
 Public Member Functions inherited from opentxs::OTInstrument Public Member Functions inherited from opentxs::OTInstrument | |
| EXPORT | OTInstrument () |
| EXPORT | OTInstrument (const OTIdentifier &SERVER_ID, const OTIdentifier &ASSET_ID) |
| virtual EXPORT | ~OTInstrument () |
| void | Release_Instrument () |
| EXPORT bool | VerifyCurrentDate () |
| EXPORT bool | IsExpired () |
| time64_t | GetValidFrom () const |
| time64_t | GetValidTo () const |
| const OTIdentifier & | GetAssetID () const |
| const OTIdentifier & | GetServerID () const |
| void | InitInstrument () |
 Public Member Functions inherited from opentxs::OTScriptable Public Member Functions inherited from opentxs::OTScriptable | |
| int32_t | GetPartyCount () const |
| int32_t | GetBylawCount () const |
| virtual EXPORT bool | AddBylaw (OTBylaw &theBylaw) |
| EXPORT OTParty * | GetParty (std::string str_party_name) const |
| EXPORT OTBylaw * | GetBylaw (std::string str_bylaw_name) const |
| EXPORT OTClause * | GetClause (std::string str_clause_name) const |
| EXPORT OTParty * | GetPartyByIndex (int32_t nIndex) const |
| EXPORT OTBylaw * | GetBylawByIndex (int32_t nIndex) const |
| EXPORT OTParty * | FindPartyBasedOnNymAsAgent (OTPseudonym &theNym, OTAgent **ppAgent=nullptr) const |
| EXPORT OTParty * | FindPartyBasedOnNymAsAuthAgent (OTPseudonym &theNym, OTAgent **ppAgent=nullptr) const |
| OTParty * | FindPartyBasedOnAccount (OTAccount &theAccount, OTPartyAccount **ppPartyAccount=nullptr) const |
| OTParty * | FindPartyBasedOnNymIDAsAgent (const OTIdentifier &theNymID, OTAgent **ppAgent=nullptr) const |
| OTParty * | FindPartyBasedOnNymIDAsAuthAgent (const OTIdentifier &theNymID, OTAgent **ppAgent=nullptr) const |
| OTParty * | FindPartyBasedOnAccountID (const OTIdentifier &theAcctID, OTPartyAccount **ppPartyAccount=nullptr) const |
| OTAgent * | GetAgent (std::string str_agent_name) const |
| OTPartyAccount * | GetPartyAccount (std::string str_acct_name) const |
| OTPartyAccount * | GetPartyAccountByID (const OTIdentifier &theAcctID) const |
| EXPORT int32_t | GetCountTransNumsNeededForAgent (std::string str_agent_name) const |
| virtual EXPORT bool | VerifyNymAsAgent (OTPseudonym &theNym, OTPseudonym &theSignerNym, mapOfNyms *pmap_ALREADY_LOADED=nullptr) const |
| virtual EXPORT bool | VerifyNymAsAgentForAccount (OTPseudonym &theNym, OTAccount &theAccount) const |
| bool | VerifyPartyAuthorization (OTParty &theParty, OTPseudonym &theSignerNym, const OTString &strServerID, mapOfNyms *pmap_ALREADY_LOADED=nullptr, mapOfNyms *pmap_NEWLY_LOADED=nullptr, bool bBurnTransNo=false) |
| bool | VerifyPartyAcctAuthorization (OTPartyAccount &thePartyAcct, OTPseudonym &theSignerNym, const OTString &strServerID, bool bBurnTransNo=false) |
| EXPORT bool | VerifyThisAgainstAllPartiesSignedCopies () |
| EXPORT bool | AllPartiesHaveSupposedlyConfirmed () |
| void | RetrieveNymPointers (mapOfNyms &map_Nyms_Already_Loaded) |
| void | ClearTemporaryPointers () |
| bool | GetHooks (std::string str_HookName, mapOfClauses &theResults) |
| OTClause * | GetCallback (std::string str_CallbackName) |
| OTVariable * | GetVariable (std::string str_VarName) |
| bool | IsDirty () const |
| bool | IsDirtyImportant () const |
| void | SetAsClean () |
| EXPORT bool | SendNoticeToAllParties (bool bSuccessMsg, OTPseudonym &theServerNym, const OTIdentifier &theServerID, const int64_t &lNewTransactionNumber, const OTString &strReference, OTString *pstrNote=nullptr, OTString *pstrAttachment=nullptr, OTPseudonym *pActualNym=nullptr) const |
| EXPORT bool | CanExecuteClause (std::string str_party_name, std::string str_clause_name) |
| bool | ExecuteCallback (OTClause &theCallbackClause, mapOfVariables &theParameters, OTVariable &varReturnVal) |
| OTScriptable () | |
| virtual | ~OTScriptable () |
| void | UpdateContentsToString (OTString &strAppend, bool bCalculatingID) const |
| virtual EXPORT void | CalculateContractID (OTIdentifier &newID) const |
| void | Release_Scriptable () |
 Public Member Functions inherited from opentxs::OTContract Public Member Functions inherited from opentxs::OTContract | |
| const char * | GetHashType () const |
| void | SetIdentifier (const OTIdentifier &theID) |
| EXPORT | OTContract () |
| EXPORT | OTContract (const OTString &name, const OTString &foldername, const OTString &filename, const OTString &strID) |
| EXPORT | OTContract (const OTString &strID) |
| EXPORT | OTContract (const OTIdentifier &theID) |
| void | Initialize () |
| virtual EXPORT | ~OTContract () |
| EXPORT void | Release_Contract () |
| EXPORT void | ReleaseSignatures () |
| virtual EXPORT bool | CreateContract (const OTString &strContract, const OTPseudonym &theSigner) |
| EXPORT bool | InsertNym (const OTString &strKeyName, const OTString &strKeyValue) |
| EXPORT void | GetName (OTString &strName) const |
| EXPORT void | SetName (const OTString &strName) |
| virtual EXPORT bool | VerifyContract () |
| virtual EXPORT void | GetIdentifier (OTIdentifier &theIdentifier) const |
| virtual EXPORT void | GetIdentifier (OTString &theIdentifier) const |
| EXPORT void | GetFilename (OTString &strFilename) const |
| EXPORT void | GetFoldername (OTString &strFoldername) const |
| virtual EXPORT bool | LoadContract () |
| EXPORT bool | LoadContract (const char *szFoldername, const char *szFilename) |
| EXPORT bool | LoadContractFromString (const OTString &theStr) |
| bool | LoadContractRawFile () |
| EXPORT bool | ParseRawFile () |
| EXPORT bool | SaveToContractFolder () |
| EXPORT bool | SaveContractRaw (OTString &strOutput) const |
| EXPORT bool | RewriteContract (OTString &strOutput) const |
| EXPORT bool | SaveContract () |
| EXPORT bool | SaveContract (const char *szFoldername, const char *szFilename) |
| virtual EXPORT void | CreateContents () |
| EXPORT void | CreateInnerContents () |
| virtual EXPORT bool | SaveContents (std::ofstream &ofs) const |
| virtual EXPORT bool | SaveContractWallet (OTString &strContents) const |
| virtual EXPORT bool | DisplayStatistics (OTString &strContents) const |
| virtual EXPORT bool | SaveContents (OTString &strContents) const |
| virtual EXPORT bool | SignContract (const OTPseudonym &theNym, const OTPasswordData *pPWData=nullptr) |
| EXPORT bool | SignContractAuthent (const OTPseudonym &theNym, const OTPasswordData *pPWData=nullptr) |
| EXPORT bool | SignWithKey (const OTAsymmetricKey &theKey, const OTPasswordData *pPWData=nullptr) |
| EXPORT bool | SignContract (const OTPseudonym &theNym, OTSignature &theSignature, const OTPasswordData *pPWData=nullptr) |
| EXPORT bool | SignContractAuthent (const OTPseudonym &theNym, OTSignature &theSignature, const OTPasswordData *pPWData=nullptr) |
| EXPORT bool | SignContract (const OTAsymmetricKey &theKey, OTSignature &theSignature, const OTString &strHashType, const OTPasswordData *pPWData=nullptr) |
| EXPORT bool | SignContract (const char *szFoldername, const char *szFilename, OTSignature &theSignature, const OTPasswordData *pPWData=nullptr) |
| virtual EXPORT bool | VerifyContractID () const |
| virtual EXPORT bool | VerifySignature (const OTPseudonym &theNym, const OTPasswordData *pPWData=nullptr) const |
| virtual EXPORT bool | VerifySigAuthent (const OTPseudonym &theNym, const OTPasswordData *pPWData=nullptr) const |
| EXPORT bool | VerifyWithKey (const OTAsymmetricKey &theKey, const OTPasswordData *pPWData=nullptr) const |
| EXPORT bool | VerifySignature (const OTPseudonym &theNym, const OTSignature &theSignature, const OTPasswordData *pPWData=nullptr) const |
| EXPORT bool | VerifySigAuthent (const OTPseudonym &theNym, const OTSignature &theSignature, const OTPasswordData *pPWData=nullptr) const |
| EXPORT bool | VerifySignature (const OTAsymmetricKey &theKey, const OTSignature &theSignature, const OTString &strHashType, const OTPasswordData *pPWData=nullptr) const |
| EXPORT bool | VerifySignature (const char *szFoldername, const char *szFilename, const OTSignature &theSignature, const OTPasswordData *pPWData=nullptr) const |
| EXPORT const OTAsymmetricKey * | GetContractPublicKey () const |
| EXPORT const OTPseudonym * | GetContractPublicNym () const |
Static Public Member Functions | |
| static void | CleanupNyms (mapOfNyms &theMap) |
| static void | CleanupAccts (mapOfAccounts &theMap) |
 Static Public Member Functions inherited from opentxs::OTCronItem Static Public Member Functions inherited from opentxs::OTCronItem | |
| static EXPORT OTCronItem * | NewCronItem (const OTString &strCronItem) |
| static EXPORT OTCronItem * | LoadCronReceipt (const int64_t &lTransactionNum) |
| static EXPORT OTCronItem * | LoadActiveCronReceipt (const int64_t &lTransactionNum, const OTIdentifier &serverID) |
| static EXPORT bool | EraseActiveCronReceipt (const int64_t &lTransactionNum, const OTIdentifier &nymID, const OTIdentifier &serverID) |
| static EXPORT bool | GetActiveCronTransNums (OTNumList &output, const OTIdentifier &nymID, const OTIdentifier &serverID) |
 Static Public Member Functions inherited from opentxs::OTScriptable Static Public Member Functions inherited from opentxs::OTScriptable | |
| static EXPORT OTScriptable * | InstantiateScriptable (const OTString &strInput) |
| static bool | ValidateName (std::string str_name) |
| static std::string | GetTime () |
 Static Public Member Functions inherited from opentxs::OTContract Static Public Member Functions inherited from opentxs::OTContract | |
| static EXPORT bool | DearmorAndTrim (const OTString &strInput, OTString &strOutput, OTString &strFirstLine) |
| static bool | AddBookendsAroundContent (OTString &strOutput, const OTString &strContents, const OTString &strContractType, const OTString &strHashType, const listOfSignatures &listSignatures) |
| static EXPORT bool | LoadEncodedTextField (irr::io::IrrXMLReader *&xml, OTASCIIArmor &ascOutput) |
| static EXPORT bool | LoadEncodedTextField (irr::io::IrrXMLReader *&xml, OTString &strOutput) |
| static bool | LoadEncodedTextFieldByName (irr::io::IrrXMLReader *&xml, OTASCIIArmor &ascOutput, const char *&szName, OTString::Map *pmapExtraVars=nullptr) |
| static bool | LoadEncodedTextFieldByName (irr::io::IrrXMLReader *&xml, OTString &strOutput, const char *&szName, OTString::Map *pmapExtraVars=nullptr) |
| static bool | SkipToElement (irr::io::IrrXMLReader *&xml) |
| static bool | SkipToTextField (irr::io::IrrXMLReader *&xml) |
| static bool | SkipAfterLoadingField (irr::io::IrrXMLReader *&xml) |
| static EXPORT bool | SignFlatText (OTString &strFlatText, const OTString &strContractType, const OTPseudonym &theSigner, OTString &strOutput) |
Protected Member Functions | |
| virtual void | onActivate () |
| virtual void | onFinalReceipt (OTCronItem &theOrigCronItem, const int64_t &lNewTransactionNumber, OTPseudonym &theOriginator, OTPseudonym *pRemover) |
| virtual void | onRemovalFromCron () |
| void | ReleaseLastSenderRecipientIDs () |
| void | SetNextProcessDate (const time64_t &tNEXT_DATE) |
| const time64_t & | GetNextProcessDate () const |
 Protected Member Functions inherited from opentxs::OTCronItem Protected Member Functions inherited from opentxs::OTCronItem | |
| OTCronItem (const OTIdentifier &SERVER_ID, const OTIdentifier &ASSET_ID) | |
| OTCronItem (const OTIdentifier &SERVER_ID, const OTIdentifier &ASSET_ID, const OTIdentifier &ACCT_ID, const OTIdentifier &USER_ID) | |
| void | ClearClosingNumbers () |
 Protected Member Functions inherited from opentxs::OTTrackable Protected Member Functions inherited from opentxs::OTTrackable | |
| void | SetSenderAcctID (const OTIdentifier &ACCT_ID) |
| void | SetSenderUserID (const OTIdentifier &USER_ID) |
 Protected Member Functions inherited from opentxs::OTInstrument Protected Member Functions inherited from opentxs::OTInstrument | |
| void | SetValidFrom (time64_t TIME_FROM) |
| void | SetValidTo (time64_t TIME_TO) |
| void | SetAssetID (const OTIdentifier &ASSET_ID) |
| void | SetServerID (const OTIdentifier &SERVER_ID) |
 Protected Member Functions inherited from opentxs::OTContract Protected Member Functions inherited from opentxs::OTContract | |
| bool | LoadContractXML () |
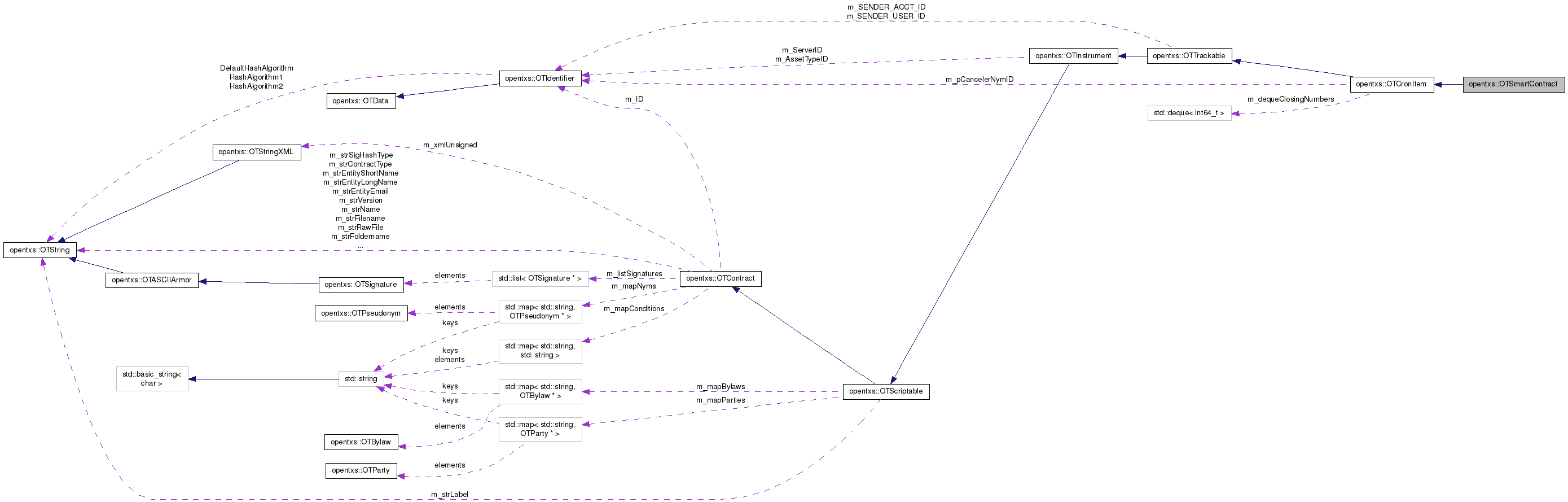
Definition at line 150 of file OTSmartContract.hpp.
| opentxs::OTSmartContract::OTSmartContract | ( | ) |
Definition at line 5335 of file OTSmartContract.cpp.
| opentxs::OTSmartContract::OTSmartContract | ( | const OTIdentifier & | SERVER_ID | ) |
Definition at line 5343 of file OTSmartContract.cpp.
|
virtual |
Definition at line 5352 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTScriptable.
Definition at line 5193 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::CanCancelContract | ( | std::string | str_party_name | ) |
Definition at line 3969 of file OTSmartContract.cpp.
|
virtual |
See if theNym has rights to remove this item from Cron.
Reimplemented from opentxs::OTCronItem.
Definition at line 4106 of file OTSmartContract.cpp.
|
static |
Definition at line 5164 of file OTSmartContract.cpp.
|
static |
Definition at line 5149 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::CloseoutOpeningNumbers | ( | OTPseudonym * | pSignerNym = nullptr | ) |
Definition at line 4976 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTScriptable.
Definition at line 5417 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTScriptable.
Definition at line 5230 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::DeactivateSmartContract | ( | ) |
Definition at line 970 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::ExecuteClauses | ( | mapOfClauses & | theClauses, |
| OTString * | pParam = nullptr |
||
| ) |
Definition at line 3761 of file OTSmartContract.cpp.
| std::string opentxs::OTSmartContract::GetAcctBalance | ( | std::string | from_acct_name | ) |
Definition at line 1182 of file OTSmartContract.cpp.
|
virtual |
| std::string opentxs::OTSmartContract::GetAssetTypeIDofAcct | ( | std::string | from_acct_name | ) |
Definition at line 1394 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 1077 of file OTSmartContract.cpp.
| int32_t opentxs::OTSmartContract::GetCountStashAccts | ( | ) | const |
Definition at line 5407 of file OTSmartContract.cpp.
| int32_t opentxs::OTSmartContract::GetCountStashes | ( | ) | const |
Definition at line 5402 of file OTSmartContract.cpp.
|
inline |
Definition at line 261 of file OTSmartContract.hpp.
|
inline |
Definition at line 257 of file OTSmartContract.hpp.
|
inline |
Definition at line 253 of file OTSmartContract.hpp.
|
inline |
Definition at line 249 of file OTSmartContract.hpp.
|
inlineprotected |
Definition at line 232 of file OTSmartContract.hpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 1062 of file OTSmartContract.cpp.
| std::string opentxs::OTSmartContract::GetRemainingTimer | ( | ) | const |
Definition at line 1124 of file OTSmartContract.cpp.
| OTStash * opentxs::OTSmartContract::GetStash | ( | std::string | str_stash_name | ) |
Definition at line 5315 of file OTSmartContract.cpp.
| std::string opentxs::OTSmartContract::GetStashBalance | ( | std::string | stash_name, |
| std::string | asset_type_id | ||
| ) |
Definition at line 1611 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 5069 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::HarvestClosingNumbers | ( | OTPseudonym * | pSignerNym = nullptr, |
| std::set< OTParty * > * | pFailedParties = nullptr |
||
| ) |
Definition at line 5008 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 5113 of file OTSmartContract.cpp.
|
virtual |
| void opentxs::OTSmartContract::InitSmartContract | ( | ) |
Definition at line 5357 of file OTSmartContract.cpp.
|
virtual |
| bool opentxs::OTSmartContract::MoveAcctFundsStr | ( | std::string | from_acct_name, |
| std::string | to_acct_name, | ||
| std::string | str_Amount | ||
| ) |
Definition at line 3119 of file OTSmartContract.cpp.
|
protectedvirtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 1156 of file OTSmartContract.cpp.
|
protectedvirtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 3377 of file OTSmartContract.cpp.
|
protectedvirtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 1141 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::PrepareToActivate | ( | const int64_t & | lOpeningTransNo, |
| const int64_t & | lClosingTransNo, | ||
| const OTIdentifier & | theUserID, | ||
| const OTIdentifier & | theAcctID | ||
| ) |
Definition at line 5589 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 3649 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 5617 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTScriptable.
Definition at line 859 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTCronItem.
Definition at line 5391 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::Release_SmartContract | ( | ) |
Definition at line 5385 of file OTSmartContract.cpp.
|
protected |
Definition at line 5571 of file OTSmartContract.cpp.
| void opentxs::OTSmartContract::ReleaseStashes | ( | ) |
Definition at line 5369 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTInstrument.
Definition at line 5770 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::SendANoticeToAllParties | ( | ) |
Definition at line 1659 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::SendNoticeToParty | ( | std::string | party_name | ) |
Definition at line 1702 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTScriptable.
Definition at line 3754 of file OTSmartContract.cpp.
|
inlineprotected |
Definition at line 228 of file OTSmartContract.hpp.
| void opentxs::OTSmartContract::SetRemainingTimer | ( | std::string | str_seconds_from_now | ) |
Definition at line 1102 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::SetServerIDIfEmpty | ( | const OTIdentifier & | theID | ) |
Definition at line 1015 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::StashAcctFunds | ( | std::string | from_acct_name, |
| std::string | to_stash_name, | ||
| std::string | str_Amount | ||
| ) |
Definition at line 1819 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::StashFunds | ( | const mapOfNyms & | map_NymsAlreadyLoaded, |
| const int64_t & | lAmount, | ||
| const OTIdentifier & | PARTY_ACCT_ID, | ||
| const OTIdentifier & | PARTY_USER_ID, | ||
| OTStash & | theStash | ||
| ) |
Definition at line 2291 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::UnstashAcctFunds | ( | std::string | to_acct_name, |
| std::string | from_stash_name, | ||
| std::string | str_Amount | ||
| ) |
Definition at line 2072 of file OTSmartContract.cpp.
|
virtual |
Reimplemented from opentxs::OTTrackable.
Definition at line 5464 of file OTSmartContract.cpp.
| bool opentxs::OTSmartContract::VerifySmartContract | ( | OTPseudonym & | theNym, |
| OTAccount & | theAcct, | ||
| OTPseudonym & | theServerNym, | ||
| bool | bBurnTransNo = false |
||
| ) |
Definition at line 4391 of file OTSmartContract.cpp.